RapidAPI
Enterprises are known to acquire business applications that are custom built, or are part of a legacy system. Often these systems are equipped with non-standard protocols and messages, which allows for security breaches and system intrusions during integration. This would risk unwanted delays and impact costing. Furthermore, support is provided by outside suppliers or business partners which is subject to availability of their support teams.

RapidAPI is a gateway solution that streamlines the management and operation of applications whilst at the same time enhancing security and regulatory compliance.
RapidAPI provides comprehensive API security and identity management integrations to deflect attacks against, control access to, and secure the data transmitted by cloud and mobile APIs, as well as traditional SOA web services. Complete auditing, monitoring, logging and reporting capabilities also help enterprises meet compliance mandates. Serving as the policy enforcement point that authenticates, authorizes and audits API access, RapidAPI protects APIs from malicious attacks as well as potential “friendly fire” by monitoring API call volume and client behaviours. Clients exhibiting disruptive behaviours can be blocked or throttled. Network firewalls do not block message-level threats, and traditional firewalls only protect Web applications.
RapidAPI can detect and prevent message level threats across all API traffic, including cloud, web, mobile and B2B channels. Messages are scanned at the protocol header, SOAP header, XML and attachment levels and REST API methods (GET, PUT, DELETE, POST, etc.) can be selectively secured to ensure that inappropriate method usage is detected and blocked.
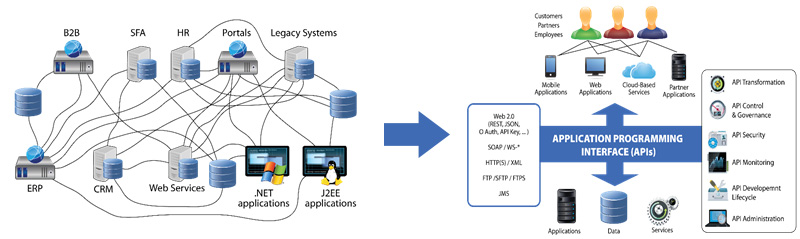
Figure 1: RapidAPI Gateway.
Features and Functions
Identity Management
RapidAPI integrates with existing third-party Identity Management (IM) infrastructures to perform authentication and authorization of message traffic. For example, integration is provided with LDAP and Microsoft Active Directory.Scalability
RapidAPI to be designed to offer a highly flexible and scalable solution architecture. Administrators can deploy new API instances as needed, and deploy the same or different policies across a group of API instances as required. This enables administrators to apply polices at any point in their system. Policy enforcement points can be distributed around the network, anywhere traffic is being passed.REST APIs
RapidAPI’s Representational State of Transfer (REST) support enables you to make enterprise application data and operations available using Web APIs. For example, you can convert a legacy Simple Object Access Protocol (SOAP) service, and deploy it as a REST API to be consumed by mobile apps. REST-to-SOAP conversion is easy to achieve using the API. It can expose REST APIs that map to SOAP services, dynamically creating a SOAP request based on the REST API call.Internationalization
RapidAPI includes support for multi-byte message data and a wide range of international languages and character sets. For example, this includes requests in languages such as Chinese, German, French, Spanish, Danish, Serbian, Russian, Japanese, Korean, Greek, Arabic, Hebrew, and so on. The API supports character sets such as UTF-8, KO-I8, UTF-16, UTF-32, ISO-8859-1, EUC-JP, US-ASCII, ISO-8859-7, and etc.Processing Offload
You can use RapidAPI to offload the heavy lifting of XML from business application servers, and on to the network. This frees up resources on application servers and enables applications to run faster. It performs Document Object Model (DOM) processing, XPath, JSON Path, XSLT conversion, and validation of XML and JSON.Data Enrichment
RapidAPI can automatically populate content in XML and JSON documents from sources such as databases. By putting this functionality on to the network infrastructure, data is automatically populated in messages before they reach the consuming services.Ease of Deployment
RapidAPI includes many features that speed up deployment. For example, certificates and private keys, necessary for XML security functions, are issued on board. The API has a deny-by-default defense posture, to detect and block unauthorized deployments of services. Policies can be re-applied across multiple endpoints using simple menus. Policies can also be imported and exported as XML files. This minimizes time needed to replicate policies across multiple API s, or to move from a staging system to production environment.Centralized Management
A web-based system management dashboard provides centralized control of API s in your domain. API Manager provides quick and easy access to enable you to manage your API s and services. For example, you can use monitoring and a traffic log to monitor messages sent through API s in your domain. All monitoring data can be aggregated across multiple API instances in a group or domain.Reporting Tools
RapidAPI Analytics tool provides auditing and reporting on usage across all entry points and creates comprehensive reports to meet operational and compliance requirements. RapidAPI Analytics also provides root cause analysis by identifying common failure points in multi-service transactions. If a service fails, and impacts the transaction as a whole, API Analytics can detect this and generate alerts.Traffic Throttling
RapidAPI protects services from unanticipated traffic spikes by smoothing out traffic. It also limits clients to agreed service consumption levels in accordance with service usage agreements. This enables customers to charge their clients for different levels of service usage.Identity Mediation
Through its support for a wide range of security standards, RapidAPI enables identity mediation between different identity schemes. For example, the API can authenticate external clients by username and password, but then issue SAML tokens that are used for identity propagation to application servers.API Management
RapidAPI enables you to secure Web APIs against attack and abuse. It also enables you to govern and meter access to and usage of Web APIs. The API provides support for API management security standards such as Open Standard to Authorization (OAuth). This enables sharing private resources with third-party websites without needing to provide credentials. Besides, it also allows user to choose from different authentication schemes, standards and token types to ensure that only valid users and applications get access to your APIs. API security must be part of the PCI compliant controls that ensure that Personal Identifiable Information (PII) is protected. APIs in PCI complaint businesses have to be hosted on infrastructure that meets the strict criteria of the PCI regulations.Application-level Networking
RapidAPI routes data based on sender identity, content, and type. This enables messages to be sent to the appropriate application in a secure manner. It also enables service virtualization, where services are exposed to clients with virtual addresses to mask their actual addresses for security and application delivery. In this way, RapidAPI acts as an important control point for network traffic by shielding endpoint services from direct access.Audit Trail
RapidAPI satisfies audit requirements by enabling service transactions to be archived in a tamper-proof store for subsequent audit. It also facilitates privacy compliance support by allowing sensitive information, such as customer names, to be encrypted or stripped out of message traffic.
Benefits of RapidAPI
- Standardized connection protocol and provides secured transfer of data.
- Minimize coding and risks of integrating systems.
- Reducing systems implementation cost and shorten deployment timeframe.
- Improved layer of security.
- Centralized reporting dashboard.